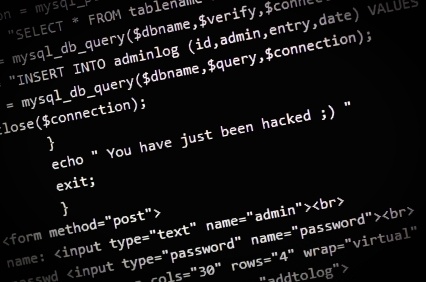
The term advanced persistent threat (APT) was originally used to describe complex, ongoing espionage perpetrated by foreign governments. However, today, APT typically refers to a category of cybercrime directed toward businesses or government entities. APTs are usually online attacks used to achieve goals beyond those that can be met by a single security breach, but some may involve malicious activity conducted onsite. Compromised computer systems are continuously monitored by the attackers or added to a stable of slave computers to be used to achieve some future goal. APTs are most often perpetrated by employing some form of malware, and IT technicians defend against APTs by installing antimalware software and hardware firewalls.
TrainACE - IT and Cybersecurity Training Blog
Ryan Corey
Recent Posts
What is Advanced Persistent Threat
[fa icon="calendar'] Dec 11, 2012 11:25:45 AM / by Ryan Corey posted in advanced persistent threat, CEH, Cisco, cyber war, Cybersecurity, Information Assurance, Pentesting, Ethical Hacking
What is Malware Analysis?
[fa icon="calendar'] Dec 4, 2012 9:23:03 AM / by Ryan Corey posted in Cisco, Cybersecurity, Information Assurance, Malware
Nearly every security breach in a company’s online network is caused by some form of malicious computer program. These programs are generally referred to as malware, but they exist in several distinct categories, including viruses, worms and Trojan horses. Being able to identify when and how malware is affecting a computer system takes specialized training, but this knowledge increases the value of any IT security technician or manager who possesses it. These individuals are capable of assessing the scope and severity of a malware infection, which leads to efficient and detailed planning of the steps required to eliminate the malware and recover any lost data or system resources.
Online Learning - A Fast Growing Force in Education
[fa icon="calendar'] Nov 7, 2012 11:44:51 AM / by Ryan Corey posted in Online Training
From the earliest days of the computer, long before the World Wide Web became a pervasive part of our lives, the role of this new machine was not restricted to government or business applications. The idea of the computer as educational tool was already up for serious discussion in the 1960s, some two decades before the “personal computer” began its conquest of the desktop.
About the CompTIA CASP Certification and Who it is Best Fit For
[fa icon="calendar'] Sep 25, 2012 7:45:31 AM / by Ryan Corey posted in CASP+, Cisco, CompTIA, Cybersecurity, Information Assurance, Ethical Hacking
The CompTIA Advanced Security Practitioner (CASP) certification is intended for professionals with at least ten years of experience in security administration. Five of those years must be hands-on technical experience. The CASP does not require that any previous exams have been passed, but is a higher-level exam than the CompTIA Security+.
The Average Computer Forensics Salary
[fa icon="calendar'] Aug 14, 2012 2:04:24 PM / by Ryan Corey posted in Salary, CHFI, Cisco, Cybersecurity, EC-Council
After the walls came down on 9/11, the walls went up on computer security. Cybercrime, computer-based terrorism, and nuisance computer hacking have become major problems in a world increasingly dependent on information technology. Computer forensic specialists have trained to uncover evidence of computer tampering not only to point out violations but also to get legal evidence for use in prosecuting criminals.
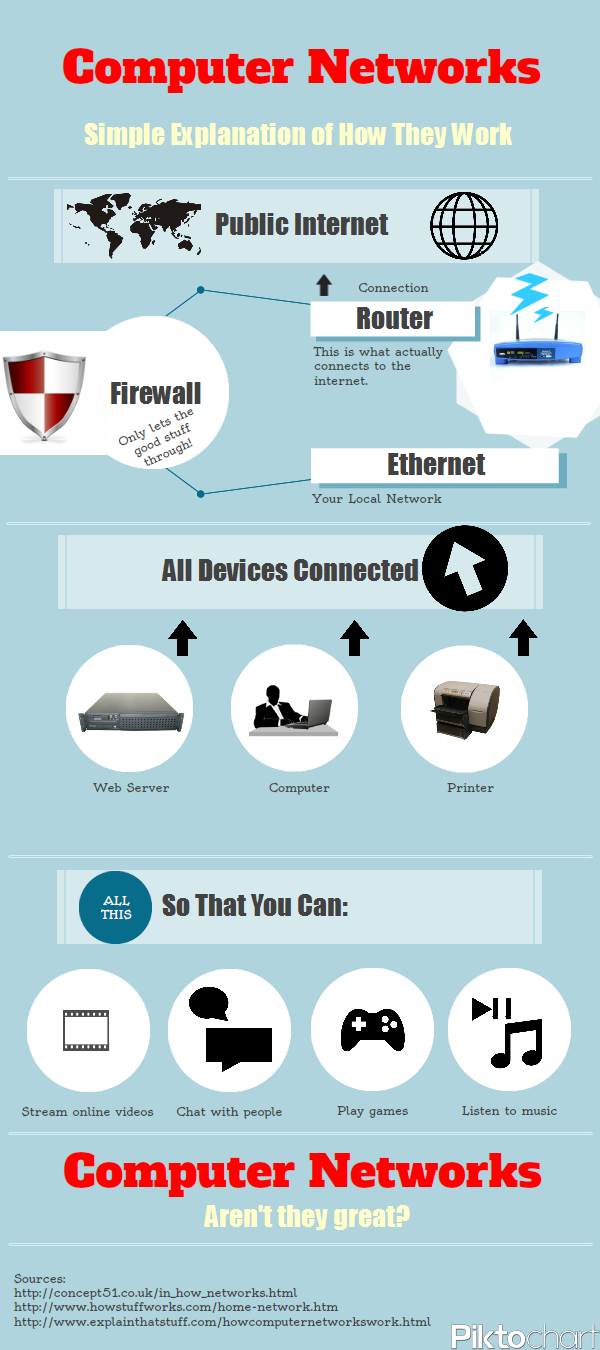
[Infographic] Computer Networks - How They Work
[fa icon="calendar'] Jun 28, 2012 1:43:08 PM / by Ryan Corey posted in CompTIA, Network+
Here's a neat little info-graphic that illustrates what goes on between your computer and the internet. Take a look at all the steps between your PC and the internet you access every day. It may seem like you just plug directly in to the internet and go, but it's a lot more complicated than that, and quite interesting!
Why Cloud Security Training Should be a Priority for Tech Firms in the Next Year
[fa icon="calendar'] Jun 7, 2012 5:08:36 PM / by Ryan Corey posted in Cloud Computing, Cybersecurity
In the last few years, businesses have started to transition over to cloud computing solutions that make it possible for them to recover data, and to save money on equipment costs. Because of the convenience that comes with cloud computing, there has been a massive movement in this area, and it is poised to get even bigger in the near future. Tech firms who want to capitalize on this phenomenon need to put an emphasis on learning security measures for the cloud.
Assessing the Changes to the New MCSE Certification
[fa icon="calendar'] Jun 1, 2012 10:08:31 AM / by Ryan Corey posted in MCSA, MCSE, Microsoft
Microsoft recently announced its plan to reintroduce the MCSE and MCSA certifications, which address the evolution of technology toward cloud computing. Many IT professionals are already aware of the MCITP certification that resulted from the Microsoft Server 2008 upgrade, but it appears the company tossed the four-year-old certification. With the reintroduction of the old but new MCSE and MCSA certifications, Microsoft also detailed that each one is not necessarily the same as it used to be.
Microsoft Certification Restructuring; Bringing Back the MCSA and MCSE
[fa icon="calendar'] Apr 19, 2012 7:23:29 AM / by Ryan Corey posted in MCSA, MCSE, Microsoft, Systems Administration, Network Administration
The expanding role of cloud computing in the IT and software development fields has Microsoft sitting up and taking notice: the company announced recently that it will be reorganizing its Microsoft certification program to address the evolving impact of the cloud. In the process, the MCSA, MCSD and MCSE certification designations will also be returned to duty, with two small changes – the “A” will now stand for “associate” instead of “administrator,” and the “E” will now stand for “expert” rather than “engineer.”
Assessing the Most Common Information Technology Careers
[fa icon="calendar'] Jan 19, 2012 2:21:54 PM / by Ryan Corey posted in Cybersecurity, Systems Administration, Network Administration
If you're thinking about pursuing a career in the information technology field, it helps to have a basic goal in terms of the kind of work that you'd like to do. There is a wide array of job titles and roles within the IT industry, and it's easy to get confused when browsing through them. One way to narrow things down is by getting a clear understanding of the differences between the industry's most common careers: network administration, systems administration, IT security and information assurance. With a firm grasp of those basic roles, you should have an easier time choosing the right career path. Learn more about each of these common information technology careers below.
How to Make a Career Change in to Information Technology (IT)
[fa icon="calendar'] Jan 11, 2012 12:40:26 PM / by Ryan Corey posted in Jobs, Uncategorized, Network+, A+
Information Technology is a reliable industry with continued growth, competitive compensation and a variety of specializations. Even in the recession-ridden decade between 2008 and 2018, job growth in the Information Technology field is expected to grow by approximately 17 percent.