On January 27, the Washington Post reported that the Department of Defense plans to expand its “Cyber Command,” a force dedicated to defending U.S. computer systems, by a factor of five, from 900 to 4,900 members. Although a formal announcement had not been made, Pentagon sources indicated that an increase in numbers was not the only change on the agenda. The Cyber Command would also undergo a shift in focus, with the new structure adding acknowledged offensive capabilities to a command that had previously been characterized as exclusively defensive.
TrainACE - IT and Cybersecurity Training Blog
Skepticism Greets Increase in Cyber Command at the Pentagon
[fa icon="calendar'] Feb 6, 2013 2:45:41 AM / by Ryan Corey posted in Cisco, Cybersecurity
How Honey Pots and Honey Farming is Used in Cyber Security
[fa icon="calendar'] Jan 29, 2013 3:45:21 AM / by Ryan Corey posted in advanced persistent threat, Cisco, Cybersecurity, Exploits, Information Assurance
The term “honeypot” or, as it sometimes appears, “honey pot,” came to computer security from the world of espionage, where it referred to an agent who would be sexually available to a target. If all went as planned, the target would be compromised, either by sexual blackmail or because the relationship led the target to share secret information.
All About the CCNA Certification Exam
[fa icon="calendar'] Jan 23, 2013 4:16:42 AM / by Ryan Corey posted in CCNA, Exams, Cisco, Networking
There is no doubt that the CCNA certification exam is considered one of the most daunting exams in the networking certification field. This exam has more first time failures than almost any other. In this post we explore some things that can help you prepare yourself better before sitting in front of that Pearson VUE testing station for the CCNA exam.
The Cyber Security Battlefield Grows More Dangerous
[fa icon="calendar'] Jan 14, 2013 10:42:28 AM / by Ryan Corey posted in advanced persistent threat, Cisco, cyber war, Cybersecurity, Information Assurance, Pentesting, Ethical Hacking
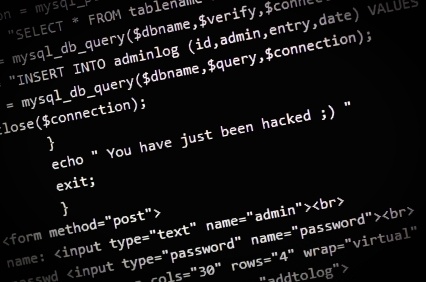
A huge portion of modern society uses some form of digital technology on a daily basis. Many conveniences on a national and personal level have been made possible due to this technology, but also opens up a Pandora's box of a whole new set of problems as well. The cyber battlefield grows more dangerous as organized hackers and other cyber threatening criminals set out to exploit the conveniences produced by the digital age for their own gain. There is an ongoing challenge, therefore, creating cyber security or defenses to protect the country from attacks; but have, on many occasions, been successfully breached to raise considerable concern even among the most savvy cyber security agencies in the world.
What is Advanced Persistent Threat
[fa icon="calendar'] Dec 11, 2012 11:25:45 AM / by Ryan Corey posted in advanced persistent threat, CEH, Cisco, cyber war, Cybersecurity, Information Assurance, Pentesting, Ethical Hacking
The term advanced persistent threat (APT) was originally used to describe complex, ongoing espionage perpetrated by foreign governments. However, today, APT typically refers to a category of cybercrime directed toward businesses or government entities. APTs are usually online attacks used to achieve goals beyond those that can be met by a single security breach, but some may involve malicious activity conducted onsite. Compromised computer systems are continuously monitored by the attackers or added to a stable of slave computers to be used to achieve some future goal. APTs are most often perpetrated by employing some form of malware, and IT technicians defend against APTs by installing antimalware software and hardware firewalls.
What is Malware Analysis?
[fa icon="calendar'] Dec 4, 2012 9:23:03 AM / by Ryan Corey posted in Cisco, Cybersecurity, Information Assurance, Malware
Nearly every security breach in a company’s online network is caused by some form of malicious computer program. These programs are generally referred to as malware, but they exist in several distinct categories, including viruses, worms and Trojan horses. Being able to identify when and how malware is affecting a computer system takes specialized training, but this knowledge increases the value of any IT security technician or manager who possesses it. These individuals are capable of assessing the scope and severity of a malware infection, which leads to efficient and detailed planning of the steps required to eliminate the malware and recover any lost data or system resources.
About the CompTIA CASP Certification and Who it is Best Fit For
[fa icon="calendar'] Sep 25, 2012 7:45:31 AM / by Ryan Corey posted in CASP+, Cisco, CompTIA, Cybersecurity, Information Assurance, Ethical Hacking
The CompTIA Advanced Security Practitioner (CASP) certification is intended for professionals with at least ten years of experience in security administration. Five of those years must be hands-on technical experience. The CASP does not require that any previous exams have been passed, but is a higher-level exam than the CompTIA Security+.
The Average Computer Forensics Salary
[fa icon="calendar'] Aug 14, 2012 2:04:24 PM / by Ryan Corey posted in Salary, CHFI, Cisco, Cybersecurity, EC-Council
After the walls came down on 9/11, the walls went up on computer security. Cybercrime, computer-based terrorism, and nuisance computer hacking have become major problems in a world increasingly dependent on information technology. Computer forensic specialists have trained to uncover evidence of computer tampering not only to point out violations but also to get legal evidence for use in prosecuting criminals.
The Average Salary for the CISSP Certification in DC, Maryland, and Virginia
[fa icon="calendar'] Jul 6, 2012 8:11:03 AM / by Paul Ricketts posted in Cisco, CISSP, Cybersecurity
UPDATED October 2022. As the cybersecurity industry matures, there are increasing opportunities for experienced infosec professionals to move into senior management roles in and around the Washington, DC, region. With the rapid rise in volume and severity of cyber threats, these roles are challenging and bring much responsibility, but they offer technologists an exciting career with lucrative salaries.
CISSP is one of the primary certifications that IT professionals can earn to prove their information security management prowess and take advantage of the opening opportunities in the field. But what is CISSP, and what is the average salary you should expect for a CISSP-related job?



/Unsplash/TrainACE%20Blog%20-%20CISSP%20Average%20Salaries.jpeg)